Security and Authentication
Looking for top-notch security for your users and data?
Discover a wide range of robust security settings designed to safeguard the personal information of your valued visitors, customers, and esteemed colleagues from any unauthorized access. CINNOX empowers you to prioritize security while elevating your communication capabilities to new heights. Experience the power of comprehensive security features and fortify your organization's defenses with CINNOX today.
CINNOX empowers its users to communicate effortlessly and effectively in a unified platform by dissolving boundaries and connecting consumers globally.
As a powerful cloud-based customer service platform, CINNOX provides businesses with robust calling and messaging capabilities on their websites and APPs, ultimately creating better engagement between service providers and their consumers.
CINNOX offers a combination of voice and chat functions, allowing you and your customers to talk and chat on a single multi-channel platform. Using CINNOX's mobile web browser or application, your agents can continue supporting your customers anywhere and anytime.
Equally important to providing effective communication, CINNOX also embraces security as a serious matter to consider. Protecting your data beyond the industry standard is one of our top priorities.
We have extensive years of experience providing satisfactory services for big and small businesses, including Fortune 500 companies.
We are proud that we have not only reached but have exceeded their requirements and expectations. This is proven by the certificates we have obtained within the telecommunications field.
Shared Security Responsibility
Security and Compliance is a shared responsibility between "You" as a Customer and "Us" as the SaaS Provider.
Our responsibility, Security Behind CINNOX, is to protect the infrastructure, including data, software, hardware, networking, and facilities that run in the service. We ensure that our service is secure so customers can focus on their work without worries.
Customer responsibility, "Security in CINNOX", is determined by the features adopted and deployed. This determines the configuration work the customer must perform as part of their security responsibilities. However, CINNOX's team handles all patch management for the operating system, network devices, and firewall. Customers will be notified of any changes but do not need to participate.
To ensure that data is protected, all data is encrypted with AES encryption before being saved to the database. All data volume on AWS or Alicloud has been encrypted with EBS encryption. The data will be stored in the customer's The home region, also known as the subscription region, usually corresponds to the legal entity region of the customer (the country where their company is registered). It is decided during the provisioning of the service and it can not be changed.. All infrastructure, data, software, hardware, networking, and facilities activities have valid audit logs, providing complete visibility and transparency for security and compliance purposes. Any activity related to the infrastructure, data, software, hardware, networking, and facilities is recorded and can be analysed for security and compliance purposes. In addition, CINNOX's internal staff, such as SREs, Operation, Customer Support and Security teams, keep track of all the logs that are part of their respective responsibilities. This allows for greater transparency and visibility into the security and compliance measures and helps ensure that customer data remains secure and protected at all times.
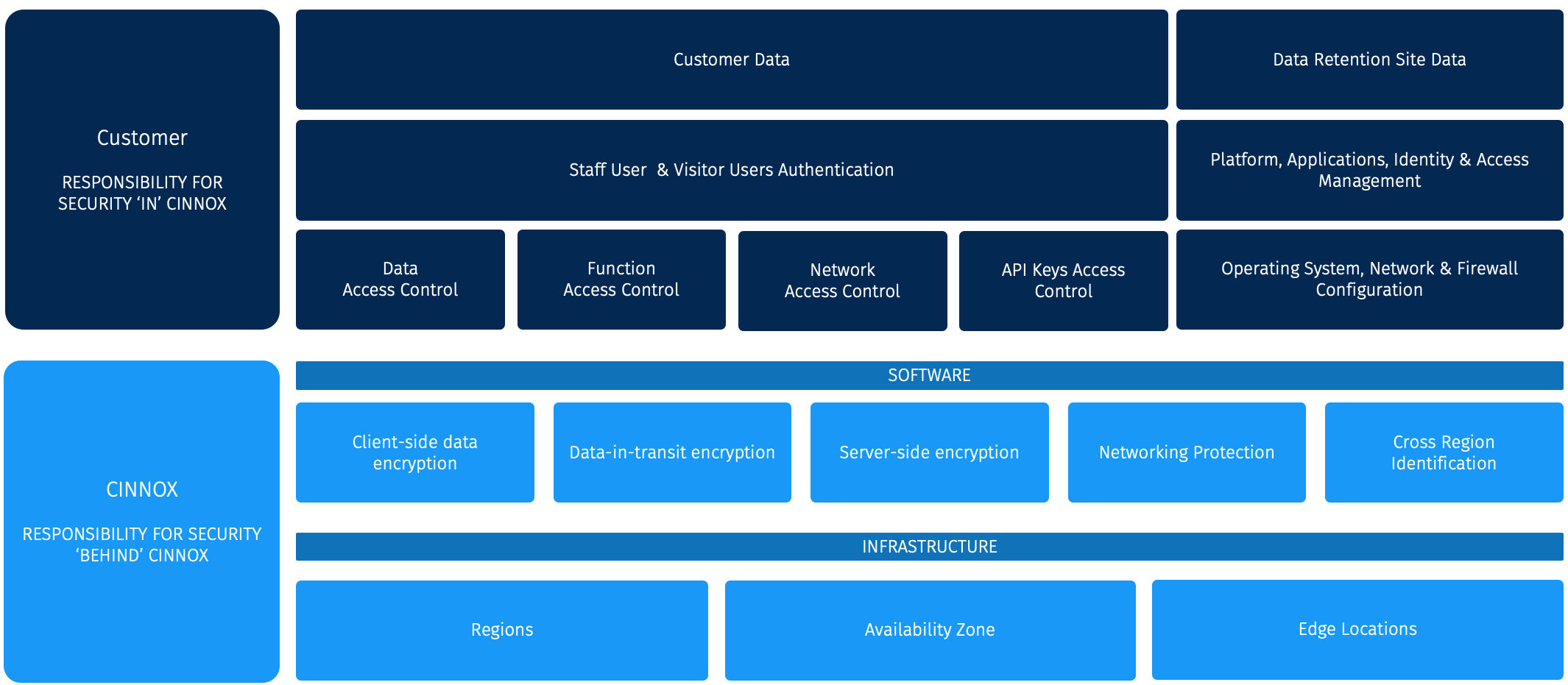
Shared Security Responsibility
Infrastructure
CINNOX's IT infrastructure is the foundation of our services, and we build it with careful technical and business planning to fulfil industry standards and business needs.
Our IT infrastructure consists of the following:
- Capacity Planning
- Availability Planning
- Continuity Planning
- Security Planning
- Business Growth Planning
CINNOX also uses multiple public clouds for better service. These tier-1 data centres are all applied to local compliance.
Our network equipment is located in multiple dedicated data centres—these house switches, servers, and network equipment that distribute our services. To fulfil the industry standards, CINNOX's network equipment is located in multiple dedicated data centres, which house switches, servers, and network equipment that distribute our services.
In addition, CINNOX also uses multiple public clouds, including AWS and Alicloud, to ensure better service. Our data is stored locally, and site replication is in place to ensure adequate redundancy and availability.
Firewall Compatibility
CINNOX uses multiple standard protocols for exchanging messages and calls. These protocols are known as firewalls.
We are using well-known ports to prevent any blockage of firewalls or proxies. Calls start via HTTPS (port 443) protocol SIP to exchange source and destination numbers. As soon as calls are connected, the media exchange on UDP 10000-50000 (DTLS-SRTP).
The exchange of messages is done through a WebSocket via HTTPS (port 443).
Client Security
Each of our customers owns a unique domain and service ID. After visitors click the widget button, we make a unique ID for each visitor related to the same domain. An authorisation is only done once, causing your visitors to be identified the next time they visit your website. However, visitors' integrity is defined and checked every time they revisit your website.
Since customer browsers can be used to hijack customer data, we implemented a high-security mechanism to mitigate this risk. A unique token that expires soon after once-off use is generated for the customer each time they visit your website. We use local storage to prevent session hijacks.
- Cross-region identification
- Secure encryption
- Secure authentication
- Audit log
- Data Retention
- Customised roles and permissions
- Private and public rooms
- Security setting to make a change for boundaries, like Call Per Minute or Message Per Minute (Advanced Throttling System)
- AI calls fraud detection and blocking
- Free DDoS prevention system
Protected agent/admin area: The control panel area is protected by username and password and has a login attempt limitation. It is designed to allow the administrator to define the password policy (password history, password age, and lockout threshold). Administrator and agent are carefully created and can only be customised for an administrator.
The administrator can also allow or block visitors/agents' access from a specific IP or number.
Room security: After visitors or agents create a new room, the following security steps are checked:
- Check if the visitor is spam or not
- Create an encrypted room and notify the agent on a secure channel
- Encrypt messages and calls during the conversation
- Prevent the sending of a lot of messages and enquiries for spamming purposes (Rate limit)
- Data encryption in transit (Using TLSv1.3 – Grade A+ from SSL Labs’ tests)
- Data encryption at rest with key rotation feature
- Unique room ID with pre-defined participants
Call security: CINNOX uses the standards-based VoIP (Voice-Over-Internet-Protocol) to deliver high-quality calls.
Features:
- High quality/reliable codec with HD to lowest bandwidth consummation (Opus), which supports other codecs as backup
- AES-256 bit TLS1.3 encryption (with supporting TLS 1.2) – Grade A+ from SSL Labs' tests
- Media encryption (DTLS-SRTP)
- Data encryption at rest to protect data
- Fraud detection and prevention
- Using global blocklist numbers to prevent spam
- Using unique EID for source and destination numbers to prevent unauthorised use
- Generating a unique temporary SIP (Session Initiation Protocol) account with AES 256-bit encryption token
Admin Controls
CINNOX has extensive years of experience in successfully defending customers from thousands of hackers. CINNOX has security features implemented in your account. It's your responsibility to protect yourself by utilising the Administration Control Features.
We offer security capabilities to manage your data access internally:
- Create a staff account with a designated role
- Customised role and permission
- Ability to create multiple companies
- Ability to create multiple departments
- Ability to assign a different role to a different department
- Suspend staff account
- Mandatory multi-factor authentication
- Enforce staff members to enable multi-factor authentication before they can log in
- Monitor staff members' usage
- Check and audit billing reports for each staff member
- Read-only audit trail for every single change
- Export feature to import to SIEM
You can customise these features to protect yourself from any suspicious activities:
- Block login after several failed attempts
- Limit the number of enquiries a visitor can make
- Limit the number of messages a visitor can send
- Detect fraudulent calls and reject them by default
- Reject requests from the hostel's IP addresses
- Detect multi-region spam
Furthermore, you can enable Data Retention to archive your data.
- When you use the Data Retention feature, you will be responsible for managing and maintaining your on-premise SFTP server (such as locally-hosted servers or preferred backup sites).
SIEM & SOC
SIEM tools are essential to the data security ecosystem: they aggregate logs from multiple systems and analyse them to catch abnormal behaviour or potential cyberattacks. A key focus is to monitor and help manage user and service privileges, directory services, and other system-configuration changes and provide log auditing, review, and incident response.
SIEM's benefit in CINNOX is identifying attackers or hackers who try to access our platform. We trace the hackers from the first access until we block them on different platforms.
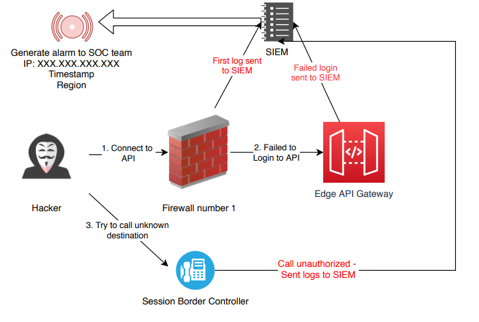
CINNOX Use Cases
- Collecting logs from all devices and applications
- Correlating logs and finding anomalies behaviours
- Using AI to find cyberattacks
- Forensics capabilities - Making proper decisions and reports for incident response
- Fraud detection and prevention by using AI algorithm
Why are we in CINNOX using SIEM?
With SIEM, we can detect a cyber attack and use AI to block bad traffic automatically. We also generate alerts for our security team; some are sent to customers to inform them of the incident.
CINNOX's SIEM can also improve incident handling activities' efficiency by reducing resource utilisation and allowing real-time incident responses, limiting the damage.
Security Operation Centre (SOC)
Our SOC team has high-level security skills for accessing different security systems like SIEM to prevent identity theft and block incidents.
CINNOX uses a 24/7 dedicated SOC team with different security certificates (CEH, CISSP, OSCP, and SANS).
Our security team is separated into different tiers. The first one monitors the graphs and alarms. They analyse and send reports to the next tier for investigation and proper action with security alerts. The action can be to block the hacker or to do a forensic process and incident handling.

Privacy & Compliance
Protecting our customers' privacy is a priority at CINNOX, and we are committed to maintaining strong and compliant privacy protections in line with the provisions of the Hong Kong Personal Data (Privacy) Ordinance (CAP 486) and the General Data Protection Regulation (EU) 2016/679. Ensuring your information's privacy is an important responsibility, and we thank you for your trust in us.
CINNOX Group's privacy policy is entirely transparent. We are committed to protecting personal data and guarantee that personal information is only used for the purposes agreed to by our customers.
CINNOX guarantees to use the best technologies and methods to protect customers' data.
CINNOX Compliance

GDPR
The General Data Protection Regulation (GDPR) is the world's toughest privacy and security law.
The GDPR primarily aims to give individuals control over their data. And simplify the regulatory environment for international business by unifying the regulations within the EU.
CINNOX guarantee to:
- Keep the personal data in a safe place and proper location based on GDPR
- Collect minimum data to improve products
- Clear and simplified policy
- Answer to customers for delete or edit personal data
- Notify customers in case of a data breach
PCI-DSS
The Payment Card Industry Data Security Standard (PCI-DSS) is a globally recognized framework that ensures businesses process, store, and transmit payment information securely. CINNOX is compliant with PCI-DSS Version 4.0, Service Provider Level 1, the highest certification level, ensuring we meet the most stringent security standards for protecting sensitive payment data.
CINNOX is committed to:
- Protecting payment data with secure encryption and secure data storage according to PCI-DSS standards.
Minimizing data collection to only what’s necessary for secure and efficient payment processing. - Maintaining a clear and transparent policy for handling sensitive information, ensuring customers are fully informed.
- Promptly notifying customers in the event of a data breach
Other Security Features
Training
We have annual security awareness training with a monthly security newsletter for our employees. Developers passed multiple security training to ensure their code was secure by default.
Security Pentest
CINNOX has been tested several times by security companies and hackers. It helps ensure our application is secure and covers the latest OWASP risks.
Sample companies:
InfoOcean: https://www.infocean.com
Ringus: https://ringus-solution.com
We perform penetration tests (pentest) annually to ensure more consistent network security management by revealing how newly discovered threats or emerging vulnerabilities might be exploited by malicious hackers.
We have vulnerability scans on our PoP sites daily to ensure new deployments or libraries are secure and not susceptible to exploits or attacks.
We have a bug bounty program for hackers. If you find a security bug, contact us at [email protected] to analyse the bug and receive your bonus.
Policies
We have implemented several policies and procedures to help protect sensitive information and ensure that only authorised employees can access critical systems and data.
One of our key policies is to restrict access to sensitive database credentials. Only trusted employees who have undergone a thorough background check and audit trail review by an independent party can access these credentials.
In addition, we use a built-in policy and password manager to generate temporal credentials after manager approval. These credentials only remain valid for a limited period (usually one hour) before they must be renewed or revoked.
All of our employees must sign a confidentiality agreement as part of their employment contract, which helps ensure they understand and respect the importance of protecting sensitive data.
We take extra precautions with critical assets that contain sensitive data, such as customer information. These assets are only accessible from a secure environment with multiple layers of security controls, including internet blocking and intrusion detection systems.
Finally, we have a mandatory leave policy for key personnel. This policy ensures that backup personnel have completed critical training and reduces the risk of fraud or other security incidents during employee absence.
Updated 5 months ago
- Chatroom
- Serving Chat Enquiries
- Sending and Receiving Chats
- Canned Responses
- Chat Translation
- AI Enquiry Summary
- AI Enquiry Summary Custom Format Best Practices
- Add Staff to an Enquiry Room
- Monitor Enquiry and Take Action
- Private Message
- Get your Azure OpenAI Account
- Integrate your Azure OpenAI Account with CINNOX
- Labelling an Enquiry
- Sharing Files
- Space (Group Chat)
- Customer Public Space (Private Chat)
- Manage Tag Directory
- Creating a Tag
- Managing Social Channels
- Connecting (FB) Messenger
- Connecting Wechat
- Connecting Whatsapp
- 360dialog (WhatsApp BSP)
- Restart the Enquiry Conversation (360dialog WhatsApp)
- Connecting Line
- Connecting Woztell
- Get a Woztell Account and Create Channels
- Connecting Email
- Connecting Gmail/Google Workspace Email
- Connecting Outlook/Microsoft 360 Email
- Email Enquiry Handling
- Connecting Third-Party Channel
- Channel Source
- Email Engagement
- Pin/Unpin Messages & Hide/Unhide Chat Rooms
- Sending SMS
- SMS Inbox
- SMS and Call Known Limitations
- Campaigns
- Creating SMS Standard Campaign
- Create SMS Dynamic Campaign
- Campaign Templates
- SMS Templates
- WhatsApp Engagement
- Creating WhatsApp Campaign
- Whatsapp Templates
- CINNOX Markdown Guide
- Managing Destinations
- Managing Service Group
- Adding Chatbot
- CINNOX Q&A Bot
- Chatbot Data Source
- Chatbot Custom Prompts Best Practices
- General Integration for Chatbot
- IVR (Interactive Voice Response)
- Alternative, Percentage, Time and Sticky Routing Rules
- Queue Settings
- CINNOX Distribution Method (ACD)
- Advanced Enquiry Routing Flow
- Enquiries in CINNOX
- Enquiry Centre
- Transferring Enquiry
- Transferring Chat
- Follow Up on Missed Enquiries
- Closing an Enquiry
- Monitoring
- Enquiries Monitoring (aka Enquiry Overview)
- Queue Monitoring
- Contacts
- Managing External Contacts
- Labelling an External Contact
- Custom Field for External Contacts
- Merging Contacts
- Integrating Salesforce
- Salesforce Contacts in Dashboard
- Engagement in CINNOX
- Developer Guide
- Prerequisites
- Installing the Web Widget
- Configure the Widget UI Language
- Passing data to agent via Weblink and Widget
- Tag Conditional Trigger
- Installing Internet Information Services (Microsoft IIS)
- Installing Apache Server
- Installing Nginx Server
- Wordpress
- Wix
- Drupal
- Joomla
- Squarespace
- BigCommerce
- Shopify
- Weebly (eCommerce by Square)
- Webflow
- HubSpot CMS Hub
- Jimdo
- Leadpages
- SHOPLINE
- Thinkific
- APPs & API
- Zapier
- CINNOX Chrome Extension
- My Sites
- Configure CINNOX Web Widget
- Customising Your Widget
- Managing Widget's Smart Greeting
- Managing Visitor Forms
- Managing Staff
- Managing Roles and Permissions
- Managing Teams
- Managing Call Recording an Transcript
- Managing Labels
- Keyword Masking
- Managing Contact & Enquiry Settings
- Managing Call Prompts
- Managing Storage
- My Plan
- Cancelling CINNOX Account
- Getting Started with the App
- App Sign In and Sign Out
- Navigating the App
- Enquiry Monitoring (aka Enquiry Overview)
- Chat Room
- Private Message
- Serving Chat Enquiries
- Serving Call Enquiries
- Monitor Chat Enquiry & Take Action
- Add Staff to an Enquiry Room
- Closing Enquiries
- Labelling an Enquiry
- Labelling External Contacts
- Sending and Receiving Chats
- Sharing Files
- Making Calls
- Answering Calls
- Sending SMS
- WhatsApp Engagement
- Email Engagement
- Instant Conference Call
- Scheduling Conference Call
- 1-to-1 to Conference
- Ongoing Conference Call
- Video Calling
- Recording and Transcript
- Following Up on Missed Enquiries
- Transferring Enquiry
- Transferring Call
- Transferring Chat
- Space (Group Chat)
- Restart the Enquiry Conversation (360dialog WhatsApp)
- Pin/Unpin Messages & Hide/Unhide Chat Rooms
- Contacts
- Merging Contacts
- Salesforce Contacts in CINNOX App
- Sync Device Contacts
- Setting Up Your Availability Status
- Unread Panel
- Mention Preference
- Conference Preference
- My Account - Staff Profile
- Changing Password
- Passcode and Biometrics
- Two-Factor Authentication
- Third-Party Authentication (Staff App Login)
- Service Numbers
- Personal Numbers
- Call Forwarding
- Managing Devices
- Simulation and Help Centre
- Sending Feedback
- Reports API
- Get Enquiry Details
- Get Enquiry Chat Details
- Get Call Details
- Get Conference Details
- Get Call Log Details
- Get Recording File Details
- Get Transcription File
- Get SMS Details
- Get Enquiry Overview Matrix
- Get Channel Type list
- Get Channel Type details
- Create/Edit/Delete Enquiry Event Subscription
- Create/Edit/Delete Recording File Event Subscription
- Create/Edit/Delete Conference Call Event Subscription
- Get Sent Campaigns Summary
- Get Sent Campaign Details
- Management API
- Create/Edit/Delete External Contact Event Subscription
- Get External Contact List
- Get External Contact Activity
- Create External Contact
- Update External Contact
- Create/Edit/Delete Contact Event Subscription
- Create/Edit/Delete Staff Contact Event Subscription
- Get Staff Contact List
- Get Supported Language List
- Get Supported Location List
- Create Destination-Service Group
- Update Destination-Service Group
- Get Destination List
- Delete Destination-Service Group
- Create Tag
- Get Tag List
- Update Tag
- Delete Tag
- Get Label List
- Delete Label
- Label an Enquiry
- Unlabel an Enquiry
- Create/Edit/Delete Label Event Subscription